Search This Blog
Monday, 24 May 2021
Deadline For SCA On E-commerce Transactions Slips Again
Sunday, 7 February 2021
UK Changes To Strong Customer Authentication and Payments Guidance
Specifically, the FCA is changing the regulatory technical standards applicable to strong customer authentication (SCA) to:
- create a new SCA exemption in Article 10A so that a customer's payment account provider (ASPSP) does not need to require the customer to reauthenticate every 90 days when accessing account information through an account information service provider (AISP or TPP);
- limit the scope of the existing Article 10 exemption to when the customer accesses their information directly;
- add a requirement where a TPP continues to accesses account information where the customer does not actively request, the TPP will need to reconfirm the customer’s explicit consent every 90 days and disconnect access/stop collecting data if a customer fails to re‑confirm their consent.
- require certain ASPSPs to allow access by TPPs to payment accounts via 'dedicated interfaces' rather than modifed customer interfaces for personal and SME ‘current accounts’ ("payment accounts" under the Payment Account Regulations) and credit card accounts held by consumers or SMEs.
- require that the technical specifications and testing facility only be made available to TPPs from the launch of new products and services, rather than 6 months in advance and that the requirement for a fallback interface should only take effect six months after launch.
- allow ASPSPs to rely on exemptions
from setting up a fallback interface granted by home state competent authorities;
- amend the threshold at which SCA must be applied to a single payment from £45 to £100-£120 and the threshold value for cumulative contactless payments from £130 to £200.
In addition, the FCA will amend its guidance in the "Approach Document" on how it supervises SCA to be consistent with the above changes and with existing EBA and European Commission guidance as follows:
- SCA would need to be reapplied where the final amount of a payment is higher than the original amount authorised, so long as the final payment is reasonably within the amount the customer agreed to when authorising the payment and not higher by more than 20% and the customer has agreed to the possibility before authorising the original amount.
- the payee’s PSP (e.g. merchant acquirer) should be liable where it triggers an SCA exemption and the transaction is carried out without applying SCA, so (other than where the
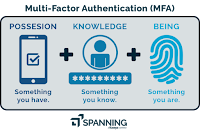
payer has acted fraudulently) the payer’s PSP would refund the customer and be entitled to reimbursement by the payee’s PSP. - for the purpose of what can be used to satisfy two of the three SCA authentication factors (knowledge (something only the user knows), possession (something only the user possesses) and inherence (something the user is)): a device could only be used as evidence of 'possession' where there is a reliable means to that the device is actually in the customer's possession; static card data cannot satisfy either the 'knowledge' or 'possession' factor; behavioural biometrics may satisfy the 'inherence' factor (as they ‘relate to physical properties of body parts, physiological characteristics and behavioural processes created by the body.
and any combination of these) but not other individual properties, such as spending patterns. - the fraud rate calculation used to anyalyse whether transaction risk is low enough to justify the exemption from SCA should only include unauthorised or fraudulent remote electronic transactions for which the PSP was liable, and no other types of transactions (unlike the calculation for payments fraud reporting under REP017).
- the corporate exemption is applicable to cards or payment instruments that are ‘only
available to payers who are not consumers’, i.e. only available to corporate customers. - the authentication elements the customer uses to access their payment account online (including via a mobile) may be reused if they then initiate a payment within the same online session), so a customer could authenticate the payment only one extra element where the firm relies on the account log-in password, for example (as long as the dynamic linking element is linked to the SCA element used when the payment is initiated).
- merchant-initiated transactions: transactions initiated by the payee only, without any involvement from the payer, are not in scope of SCA. While card‑based payments generally imply an action by the payer and are considered as 'transactions initiated by the payer, through the payee',
where a payer has given a mandate to the payee/merchant for a transaction, or series of
transactions, made using a card or other payment instrument then the payments
initiated pursuant to this mandate are outside of the scope of SCA That includes payments made under continuous payment authorities such as a subscription for a streaming service, but SCA is required to set up the mandate. - in order to monitor the contactless exemption thresholds, firms use a counter that is either host‑based, on a device (which won't count offline transactions); or chip‑based, on the physical card, (which will count both online and offline transactions), but in either case firms should consider the risk of unauthorised or non‑compliant contactless transactions being made and monitor the effects of the option in practice.
- clarify that ASPSPs must share with payment information service providers (PISPs): the name of the account holder (if the name is shown to the customer in their online account); and the account number and the sort code (if these are shown to the customer after they make a payment).
- reflect the fact that ASPSPs must accept at least one other electronic means of identification issued by an independent party, in addition to eIDAS certificates (Article 34 of the SCA‑RT).
The FCA will also amend its guidance in the "Approach Document" on how it more generally supervises the regulation of e-money and payment services to:
- make the temporary Covid19 guidance on safeguarding permanent and to extend guidance on risks and controls relating to the insurance method of safeguarding to the guarantee method of safeguarding;
- include guidance on the Treasury's proposed special administration regime for e-money and payment institutions;
- reflect the extension of the FCA’s Principles for Businesses to the provision of payment services and issuing of e‑money by certain PSPs and e‑money issuers;
- reflect the application of certain communication rules and guidance in the Banking Conduct of Business Sourcebook (BCOBS) to communications with payment service and e‑money customers and the communication and marketing of currency transfer services;
- clarify the FCA's expectations on notifications under the electronic communications exclusion (ECE) and limited network exclusion (LNE) including more detail on the types of information expected as part of a firm’s notification and the types of firms that may be able to benefit from the LNE;
- update certain reporting requirements;
- reflect changes following EU withdrawal and the end of the transition period, and the application of our rules and guidance to firms in one of the temporary permission schemes designed to replace passporting as the basis for EEA-based EMIs, PIs and RAISPs to continue operating in the UK for 3 years after the end of the transition period.
If you need assistance on any of these issues, please let me know.
Tuesday, 9 June 2020
New EBA Guidance On Obstacles And Interfaces: Open Payments Under PSD2
 |
| Source: Payments Cards & Mobile |
• the types of authentication procedures that ASPSPs’ interfaces are required to support;
• whether mandatory redirection at the point-of-sale is an obstacle;
• whether multiple Strong Customer Authentications (SCA) can be required;
• whether the 90-days re-authentication requirement can be relaxed;
• the extent to which manual account input/selection is an obstacle;
• whether additional checks on customer consent can be required; and
• what additional registrations might be permissible.
- the TPP can seek its customer's consent to retrieve the list of all her accounts with the ASPSP via the ASPSP's interface and display it to the customer in the TPP's system, so she can select the account and the TPP can then request access or initiate a payment using the account details; or
- if the ASPSP has implemented a redirection or decoupled approach and the TPP does not extract and then transmit the account details to the ASPSP with its customers' request, the customer could select the relevant account(s) on the ASPSPs’ domain during the ASPSP's authentication procedure, in a way that is no more complicated than selecting the account(s) directly with the ASPSP (e.g. via a drop-down list of accounts, or prepopulated account details if only one).
Monday, 25 May 2020
The End Of Unilateral Change In Contracts For Payment Services? No! [Updated]
This post examines the view of the AG (and the Austrian court) that a payment service provider can only rely on the regulation allowing automatic changes to its contracts for "non-essential changes", citing German court rulings that such acceptance "cannot extend to substantial contractual changes."
Why is this important?
These practicalities are recognised in the recitals to PSD2:
(57) In practice, framework contracts and the payment transactions covered by them are far more common and economically significant than single payment transactions. If there is a payment account or a specific payment instrument, a framework contract is required.
(60) The way in which the required information is to be given by the payment service provider to the payment service user should take into account the needs of the latter as well as practical technical aspects and cost-efficiency depending on the situation with regard to the agreement in the respective payment service contract.
(63) In order to ensure a high level of consumer protection, Member States should, in the interests of the consumer, be able to maintain or introduce restrictions or prohibitions on unilateral changes in the conditions of a framework contract, for instance if there is no justified reason for such a change.
What does PSD2 allow?
The relevant provisions of PSD2 are as follows:
‘framework contract’ means a payment service contract which governs the future execution of individual and successive payment transactions and which may contain the obligation and conditions for setting up a payment account;
Article 51 Prior general information
1. Member States shall require that, in good time before the payment service user is bound by any framework contract or offer, the payment service provider provide the payment service user on paper or on another durable medium with the information and conditions specified in Article 52...
2. If the framework contract has been concluded at the request of the payment service user using a means of distance communication which does not enable the payment service provider to comply with paragraph 1, the payment service provider shall fulfil its obligations under that paragraph immediately after conclusion of the framework contract.
3. The obligations under paragraph 1 may also be discharged by providing a copy of the draft framework contract including the information and conditions specified in Article 52.
Article 52 Information and conditions
Member States shall ensure that the following information and conditions are provided to the payment service user:...6. on changes to, and termination of, the framework contract:
(a) if agreed, information that the payment service user will be deemed to have accepted changes in the conditions in accordance with Article 54, unless the payment service user notifies the payment service provider before the date of their proposed date of entry into force that they are not accepted;...
(c) the right of the payment service user to terminate the framework contract and any agreements relating to termination in accordance with Article 54(1) ...
Article 54 Changes in conditions of the framework contract
1. Any changes in the framework contract or in the information and conditions specified in Article 52 shall be proposed by the payment service provider in the same way as provided for in Article 51(1) and no later than 2 months before their proposed date of application. The payment service user can either accept or reject the changes before the date of their proposed date of entry into force.
Where applicable in accordance with point (6)(a) of Article 52, the payment service provider shall inform the payment service user that it is to be deemed to have accepted those changes if it does not notify the payment service provider before the proposed date of their entry into force that they are not accepted. The payment service provider shall also inform the payment service user that, in the event that the payment service user rejects those changes, the payment service user has the right to terminate the framework contract free of charge and with effect at any time until the date when the changes would have applied.
2. Changes in the interest or exchange rates may be applied immediately and without notice, provided that such a right is agreed upon in the framework contract and that the changes in the interest or exchange rates are based on the reference interest or exchange rates agreed on in accordance with point (3)(b) and (c) of Article 52...
Secondly, there is no distinction made for the type of changes to the framework contract that can be covered by the unilateral change process, except to say that changes in interest or exchange rates based on agreed reference may be applied immediately and without notice, if that is also agreed.
Consumer Protection
- any clause in a business-to-business contract that is subject to the Unfair Contract Terms Act 1977 (UCTA) which allows a party to perform in a way that is substantially different to what was reasonably expected will be void unless it passes the test of reasonableness;
- various terms giving traders the unilateral right to change the terms of a contract, the characteristics of the products supplied or the price payable under the contract are grey-listed in the Consumer Rights Act 2015 under suspicion of being unfair, with an exception for financial services contracts (particularly those for an indefinite duration) that reflects the type of mechanism specified in PSD2 (paragraphs 21-23 of Schedule 2);
- the courts may imply a term that such a right must not be exercised capriciously, arbitrarily or for an improper purpose (Nash v Paragon Finance), except in the case of a decision whether to exercise an absolute contract right (The Product Star (2)).
In the case at hand, my view is that the unilateral change clause is not of itself unfair or unreasonable etc., but the clauses that wrongly claim the bank is unable to prove a payment was authorised or is technically unable to block contactless use might be impeached (whether under UCTA, or on grounds of mistake etc as explained in previous posts).
Post Script 17.11.20
Great news! The ECJ has held that the unilateral change mechanism in PSD2 (Directive 2015/2366) can be used for both consumer/micro-enterprise customers and larger corporate customers (subject to the corporate opt-out) and there is no limit to the type of contractual changes that can be made using the unilateral change mechanism under PSD2. However, where the customer is a consumer the changes themselves can be assessed for unfairness under the Unfair Terms in Consumer Contracts Directive 1993 (Directive 93/13):
Consequently, the answer to the first question is that Article 52(6)(a) of Directive 2015/2366, read in conjunction with Article 54(1) thereof, must be interpreted to the effect that it governs the information and conditions to be provided by a payment service provider wishing to agree, with a user of its services, on tacit consent with regard to changes, in accordance with the detailed rules laid down in those provisions, of the framework contract that they have concluded, but does not lay down restrictions regarding the status of the user or the type of contractual terms that may be the subject of such tacit consent, without prejudice, however, where the user is a consumer, to a possible review of the unfairness of those terms in the light of the provisions of Directive 93/13.
Tuesday, 19 May 2020
Can A Bank Make You Agree That Your Card Cannot Be Blocked When It Actually Can Be Blocked?
Of course, under English law, these facts would also raise issues under the law of mistake, which can affect the formation, existence and enforceability of the contract.
Post Script 17.11.20
The ECJ has agreed with the AG:
"...a payment service provider wishing to exercise the option provided for in Article 63(1)(a) of Directive 2015/2366 may not, in order to relieve itself from its own obligations, simply state, in the framework contract relating to the payment instrument concerned, that it is unable to block that instrument or to prevent its further use. That service provider must establish, with the burden of proof being on that provider in the event of a dispute, that that instrument in no way allows, on account of technical reasons, its blocking or prevention of its further use. If the court hearing those proceedings considers that it would have been physically possible to carry out such blocking or to prevent such use, having regard to the objective state of available technical knowledge, but that the provider did not make use of that knowledge, Article 63(1)(a) may not be applied to the benefit of that provider."
This is inconsistent with the findings on anonymity, however, where the ECJ was prepared to simply accept as fact that the issuer of NFC functionality is unable to establish who used the card in that mode (when that does not seem to be the case and/or technology may evolve to put that beyond doubt).
If an issuer could prove that the instrument does not allow blocking or prevention of further use, then it could agree with the user in the customer contract to disapply:
- the requirement of the user to inform the provider without delay of the loss, theft, misappropriation or any unauthorised use of the payment instrument concerned;
- the need for the provider to make available to the user means to make that notification free of charge or to request unblocking of that instrument; and
- the provision which relieves the payer from the financial consequences of any use of the lost, stolen or misappropriated instrument that takes place after that notification (except where he or she has acted fraudulently).
Sunday, 17 May 2020
Are [Low Value] Contactless Card Payments "Anonymous"? Yes! [Updated]
In this case, the bank stated in its card terms (the "framework contract") that it "shall not have to prove" and it "is unable to prove" that low value transactions were authorised and not defective.
- Low-value transactions: up to €30 per transaction (limit of five separate transactions or €100);
- Recurring transactions: e.g. subscriptions for the
same amount and payee (SCA applied to the first transaction);
- Whitelisted: payers can add payees to a
whitelist of trusted beneficiaries with the issuer,
but payees can't request this;
- Corporate payment processes: dedicated process for non-consumers, approved by the regulator (member
states may exclude micro-enterprises as consumers);
- Contactless: up to €50 (limit of five separate transactions or €150 without an SCA check);
- Unattended terminals: only for paying transport fares or parking fees;
- Low-risk of fraud: as determined by the issuer,
depending on its average fraud levels for the relevant acquirer (not by merchant/channel), with
different limit for cards and credit transfers.
Therefore, the regulatory SCA requirement introduces a significant regulatory challenge to the 'anonymous' use of a card's contactless functionality. It merely dictates that an issuer may allow the use of the card without the security credentials in seven scenarios, the contactless scenario being merely one.
It would also be wrong, however, to conclude (as the Advocate General has) that contactless payments would not themselves "not subject to the obligation of strong customer authentication". The regulatory SCA standard requires that the customer's contactless use must be challenged by the requirement to provide her security credentials, either every fifth time she uses it or when a total transaction value of €150 is reached. This will result in the attempted contactless use being prevented, and an invitation to insert the card in the relevant terminal into which the credentials can be entered.
Post Script 17.11.20
The ECJ has agreed with the AG:
"...the use of the NFC functionality for the purpose of making low-value payments constitutes ‘anonymous’ use, within the meaning of Article 63(1)(b) of [PSD2], even where the card equipped with that functionality is associated with the bank account of a particular customer. In such a situation, the payment service provider is objectively unable to identify the person who paid using that functionality and thus unable to verify, or even prove, that the transaction was duly authorised by the account holder...
...a contactless low-value payment using the NFC functionality of a personalised multifunctional bank card constitutes ‘anonymous’ use of the payment instrument in question, within the meaning of that derogation provision.
Yet this is not only inconsistent the facts, in my view, but also with the ECJ's own finding in relation to the question of whether the instrument allows blocking or prevention of further use in Article 63(1)(a), where the ECJ held the bank bears the onus of proof in order to rely on the derogation. While in that respect the bank was not allowed to merely assert in the contract that it is impossible to block the payment instrument concerned or to prevent its continued use, where, in the light of the objective state of available technical knowledge, that impossibility cannot be established; here the ECJ has done that job for the bank!
Where this leaves the use of SCA in relation to NFC payment transactions is unclear, but banks and other payment servicer providers who issue NFC functionality may agree with customers that:
- the provider need not prove the authentication and execution of payment transactions;
- the service provider is not liable for unauthorised payment transactions; and
- the payer loses the cap of EUR 50 on losses resulting from such transactions, after notification to the provider of the loss, theft or misappropriation of the payment instrument.
Wednesday, 13 May 2020
Is The Contactless Payment Function In a Payment Card a Separate Payment Instrument? Yes! [Updated]
This matters, because PSD2 would apply differently to contactless payments if they were carried out using a separate payment instrument, rather than as just another card payment.
[Update, Spoiler alert 17.11.20: the ECJ has agreed with the AG! See end of this post]
"any personalised device and/or set of procedures agreed between the payment service users and the payment service provider and used in order to initiate a payment order".
- personalised, which is to say that they allow the payment service provider to verify that the payment order was initiated by a user authorised to do so; or
- anonymous or non-personalised, in which case the payment service providers are not required to prove that the transaction in question was authenticated.
But in my view this distinction should be irrelevant in the present case, since the contactless use of an NFC-enabled payment card is neither "anonymous" nor "non-personalised", as I'll explain in my next post on the second issue being referred to the ECJ. However, the Advocate General clearly relies quite heavily on the scope for non-personalised payment instruments in his view that the contactless feature is a payment instrument in its own right.
Is NFC functionality of a payment card a separate payment instrument?
It seems unnecessary to get into all of the technical detail of how near-field communication (NFC) or the other technology enables the use of a payment card to be used 'contactlessly' by waving it near a terminal to initiate the relevant payment transactions, rather than swiping the card or inserting it into the terminal and entering a personal identification number (PIN). The AG's opinion refers to technological "formats based mainly on ISO 14443", but it should be noted that the industry actually develops NFC solutions to the EMV specification that began with contact-based Chip and PIN (under ISO/IEC 7816 for contact cards) and contactless functionality [note, you must agree EMVCo's terms to access the spec]. I think that's an important sign-post to the many stakeholders and systems potentially impacted by the case in point.
The first Austrian court held that the contactless feature was not to be viewed as a distinct low-value payment instrument, because the same card could be used to make other payments. The regional appeal court held that the contactless functionality just creates a separate processing category, like mail-order telephone order (MOTO), but for low-value purchases; and it is personalised by virtue of being protected by the need for a PIN to be entered from time to time.
However, the Advocate General has said that a 'multifunctional' payment card features two different payment instruments:
- a personalised device which requires the use of one or two security elements (strong authentication) and is reserved for payments from a certain value;
- a set of procedures for making low-value payments without using those security elements, via NFC functionality.
Furthermore, it is a legal requirement under the regulatory technical standard that requires strong customer authentication (SCA) that the security credentials must be applied, unless the issuer of the payment instrument/account to which the security credentials relate applies any of the following exemptions:
- Low-value transactions: up to €30 per transaction (limit of five separate transactions or €100);
- Recurring transactions: e.g. subscriptions for the
same amount and payee (SCA applied to the first transaction);
- Whitelisted: payers can add payees to a
whitelist of trusted beneficiaries with the issuer,
but payees can't request this;
- Corporate payment processes: dedicated process for non-consumers, approved by the regulator (member
states may exclude micro-enterprises as consumers);
- Contactless: up to €50 (limit of five separate transactions or €150 without an SCA check);
- Unattended terminals: only for paying transport fares or parking fees;
- Low-risk of fraud: as determined by the issuer,
depending on its average fraud levels for the relevant acquirer (not by merchant/channel), with
different limit for cards and credit transfers.
Therefore, the regulatory SCA requirement cannot be seen as determinative of what amounts to a payment instrument. It merely dictates that an issuer may allow the use of the card without those credentials in seven scenarios, the contactless scenario being one.
It is worth noting that the Advocate General does not contend that the use of a payment card in each of the other scenarios benefiting from an exemption from SCA also constitutes a "payment instrument" in its own right.
In any case, there is only one set of credentials issued per card (it's hard enough for consumers to remember one PIN etc per card, let alone multiple PINs for different uses of the card!). Neither the industry EMV standard nor the regulatory SCA standard dictates distinct security credentials for different uses of the card.
It is also wrong, therefore, to conclude (as the Advocate General has) that contactless payments are themselves "not subject to the obligation of strong cusotmer authentication". The regulatory SCA standard requires that the customer must be challenged to provide her security credentials either every fifth time she uses it or when a total transaction value of €150 is reached. This will result in the attempted contactless use being prevented, and an invitation to insert the card in the relevant terminal into which the credentials can be entered.
The Advocate General also believes that making the contactless feature a distinct payment instrument is also justified by the need for users of NFC-enabled cards to receive "enhanced protection" and to promote fair and transparent competition between the issuers of such cards. However, PSD2 already addresses these points insofar as any payment service provider who fails to apply SCA (unless the issuer has applied an exemption) will be liable for any resulting unauthorised transaction, and could face enforcement action (now delayed to 14 September 2021))
The Portuguese and Czech governments also made submissions in the latest appeal to the effect that the contactless feature of a payment card is not a distinct payment instrument ("any personalised device and/or set of procedures agreed between the payment service users and the payment service provider and used in order to initiate a payment order"). The Portuguese pointed out that not even cards themselves are mentioned in the definiton of payment instrument, yet are specifically mentioned elsewhere in PSD2 as ways of initiating payment transactions. The Czechs said the contactless functionality is merely one of the ways the card can be used.
I would go further by focusing on the fact that contactless use of a payment card does not alter the effect of using the card to "initate a payment order". Recital 68 of PSD2 explains:
The use of a card or card-based payment instrument for making a payment often triggers the generation of a message confirming availability of funds and two resulting payment transactions. The first transaction takes place between the issuer and the merchant’s account servicing payment service provider, while the second, usually a direct debit, takes place between the payer’s account servicing payment service provider and the issuer. Both transactions should be treated in the same way as any other equivalent transactions.
Nothing turns on the use of both the terms "card" and "card-based payment instrument". These are used interchangeably in the recitals to PSD2. In the main text of PSD2, the term "card-based" is generally used to refer to any payment instrument/transaction involving a payment card. The only exception is that the expression "execution of payment transactions through a payment card or a similar device" is included among the activities that constitute the "Execution of a payment transaction" which is are two types of regulated "payment service" (depending on whether credit is also involved). So, if the Adocate General were correct in holding that the contactless element of a payment card constitutes a separate payment instrument distinct from the card, then it would follow that executing the related payment transactions is not a regulated activity because they are not executed "through a payment card"...
In the next post, I will address the Advocate General's view that making low-value contactless payments with a multifunctional card means the cardholder is using the card "anonymously" (which would mean contactless payments are not subject to the obligation of strong customer authentication in the relevant PSD2 regulatory technical standard mentioned above.
Tuesday, 12 May 2020
Red Alert: European Court Is Told That The Contactless Feature of a Payment Card is a Separate Payment Instrument!
Briefly stated, a series of questions has been referred by the Austrian Supreme Court to the European Court of Justice and, alarmingly, the Advocate General has given his opinion to the effect that:
- The contactless feature of a credit or debit card is a separate payment instrument in its own right.
- Making low-value contactless payments with a multi-functional card means the cardholder is using the card "anonymously" (and this means contactless payments are not subject to the obligation of strong customer authentication in the relevant PSD2 regulatory technical standard).
- The issuer of the contactless feature can only use the low-value exclusions from liability for unauthorised transactions in PSD2 if the issuer can show that it is not technically feasible to block the card or prevent further use of the payment instrument if it is lost, stolen, misappropriated or used without authorisation.
- The unilateral change mechanism for amending payment services 'framework' contracts cannot be applied to "the essential elements" of the contract, such as those used to add contactless functionality to a payment card (i.e. another payment instrument).
The third issue is a question of fact. In this particluarly case the issuer appears to have created a problem for itself by inserting factually inaccurate provisions in its card terms, so that "according to the framework contract" it was not technically feasible to block contactless use, even though it really is possible to decline the transactions on a stolen card.
The fourth is a really awkward twist in the tale, since it introduces huge practical challenges - and costs - for all payment service providers seeking to update their contracts to introduce new products and features, as well as aggravation for their customers.
The Facts
Wednesday, 6 May 2020
FCA Delays SCA... Again
Monday, 6 April 2020
FCA Turns Blind Eye To SCA For Contactless Card Payments
"...we are very unlikely to take enforcement action if a firm does not apply strong customer authentication when the cumulative amount of transaction values has exceeded EUR 150 or five contactless transactions in a row. But this is only as long as the firm sufficiently mitigates the risk of unauthorised transactions and fraud, by having the necessary fraud monitoring tools and systems in place and taking swift action where appropriate."
Meanwhile, the date for applying regulatory standards to secure communications amongst PSPs was also deferred from 19 September 2019 to 14 March 2020, yet some PSPs have not complied. The FCA is also letting them off the hook, where they are "facing further delays due to coronavirus:
"...we will consider on a case-by-case basis the appropriate further measures. In doing so, we will in particular consider:
- firms’ security around authentication to access their online banking and when making payments;
- their controls and processes to reduce fraud;
- whether that impact is likely to be exacerbated given the current circumstances."
Wednesday, 14 August 2019
UK Delays Anti-fraud Measures For Banking And Payments
Update: The FCA has also written to the CEOs of payment service providers it supervises, commending the plan from the trade body, UK Finance for meeting the deferred timeline. This will see SCA phased-in from Feb 2020 for merchants who are ready, with support from the card schemes in driving the adoption of the 3D Secure protocol (3DS 2.1/2) from March/September 2020.
It will be interesting to see how much progress is really made in the next 6 to 18 months...
Monday, 24 June 2019
EBA Gives Some Leeway On SCA
Whether payments are affected depends on whether PSD2 applies - some may be out of scope based on currency or location, while others may be within the scope of PSD2 but excluded. There is then a question whether the transaction is interpreted to be one caught by the SCA requirement. Is it remote or electronic and initiated by the payer (rather than being a 'merchant initiated transaction')? Even transactions that are in scope may not be caught if the issuer (not the merchant or acquirer) of the payment instrument/account applies any of the potential exemptions:
- Low-value transactions: up to €30 per transaction (limit of five separate transactions or €100);
- Recurring transactions: e.g. subscriptions for the
same amount and payee (SCA applied to the first transaction);
- Whitelisted: payers can add payees to a
whitelist of trusted beneficiaries with the issuer,
but payees can't request this;
- Corporate payment processes: dedicated process for non-consumers, approved by the regulator (member
states may exclude micro-enterprises as consumers);
- Contactless: up to €50 (limit of five separate transactions or €150 without an SCA check);
- Unattended terminals: only for paying transport fares or parking fees;
- Low-risk of fraud: as determined by the issuer,
depending on its average fraud levels for the relevant acquirer (not by merchant/channel), with
different limit for cards and credit transfers.